
See What's Included
In Your Package
Endpoint Protection
Offline & Offsite Backup


Employee Awareness Training
Our team of experts will be sure to educate you and your team through ongoing training sessions and periodically mock phishing emails to test your employees’ awareness. Companies can schedule employee training as often as they like, at times that work for their team! There is no limit on the amount of training sessions, however, we recommend monthly or quarterly sessions depending on your company.
Dark Web Monitoring
The dark web is a place where personal information can be bought and sold. Dark Web Monitoring helps shine a light on the dark web, notifying you if there is a potential breach of your company’s information. We look for evidence of account compromises and watch for PII (Personally Identifiable Information) such as home addresses and social insurance/social security numbers.

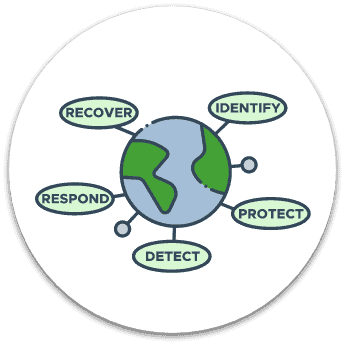
NIST Cybersecurity Framework Guidance
QuickProtect follows a globally recognized set of cybersecurity guidelines to help companies manage risk. The National Institute of Technology (NIST) created the Cyber Security Framework (CSF) as a voluntary framework to provide organizations with guidance on preventing, detecting, and responding to cyberattacks. QuickProtect satisfies several controls; our service allows companies to track and document what they’re doing. We help businesses demonstrate to their customers that they’re making reasonable efforts to protect their data.
24/7 On-Demand Cybersecurity & IT Assistance
Cyber attacks don’t stop at the end of the workday, and neither do we. At QuickProtect, we understand anything can happen at any time – that’s why we provide 24/7 On-Demand Cybersecurity & IT Assistance. Our service is always available to you, but you only pay for it if you use it!


Email Inbox Protection (Office365 and Google Workspaces Only)
Intelligent Web Browsing Protection

360Protect (Protection & Recovery Assistance)
It includes:
- $100,000 of ransomware and business email compromise protection
- $100,000 of compliance and regulatory protection
- $50,000 of business income loss protection
- $250,000 cyber liability protection (conditions apply)


